Ethical Hacking
Kali Linux Tutorial for Beginners: What is, How to Install & Use
What is Kali Linux? Kali Linux is a security distribution of Linux derived from Debian and...
Digital Forensics is defined as the process of preservation, identification, extraction, and documentation of computer evidence which can be used by the court of law. It is a science of finding evidence from digital media like a computer, mobile phone, server, or network. It provides the forensic team with the best techniques and tools to solve complicated digital-related cases.
Digital Forensics helps the forensic team to analyzes, inspect, identifies, and preserve the digital evidence residing on various types of electronic devices.
In this digital forensic tutorial, you will learn:
Here, are important landmarks from the history of Digital Forensics:
Here are the essential objectives of using Computer forensics:
Digital forensics entails the following steps:
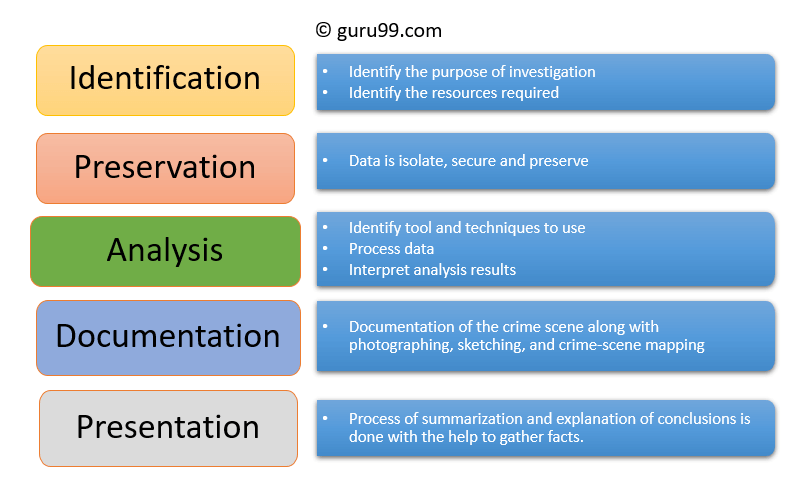
Let's study each in detail
It is the first step in the forensic process. The identification process mainly includes things like what evidence is present, where it is stored, and lastly, how it is stored (in which format).
Electronic storage media can be personal computers, Mobile phones, PDAs, etc.
In this phase, data is isolated, secured, and preserved. It includes preventing people from using the digital device so that digital evidence is not tampered with.
In this step, investigation agents reconstruct fragments of data and draw conclusions based on evidence found. However, it might take numerous iterations of examination to support a specific crime theory.
In this process, a record of all the visible data must be created. It helps in recreating the crime scene and reviewing it. It Involves proper documentation of the crime scene along with photographing, sketching, and crime-scene mapping.
In this last step, the process of summarization and explanation of conclusions is done.
However, it should be written in a layperson's terms using abstracted terminologies. All abstracted terminologies should reference the specific details.
Three types of digital forensics are:
It deals with extracting data from storage media by searching active, modified, or deleted files.
It is a sub-branch of digital forensics. It is related to monitoring and analysis of computer network traffic to collect important information and legal evidence.
It is a division of network forensics. The main aim of wireless forensics is to offers the tools need to collect and analyze the data from wireless network traffic.
It is a branch of digital forensics relating to the study and examination of databases and their related metadata.
This branch deals with the identification of malicious code, to study their payload, viruses, worms, etc.
Deals with recovery and analysis of emails, including deleted emails, calendars, and contacts.
It deals with collecting data from system memory (system registers, cache, RAM) in raw form and then carving the data from Raw dump.
It mainly deals with the examination and analysis of mobile devices. It helps to retrieve phone and SIM contacts, call logs, incoming, and outgoing SMS/MMS, Audio, videos, etc.
Here, are major challenges faced by the Digital Forensic:
In recent time, commercial organizations have used digital forensics in following a type of cases:
Here, are pros/benefits of Digital forensics
Here, are major cos/ drawbacks of using Digital Forensic
What is Kali Linux? Kali Linux is a security distribution of Linux derived from Debian and...
Ethical hacking is identifying weaknesses in computer systems or networks to exploit its...
$20.20 $9.99 for today 4.5 (112 ratings) Key Highlights of Ethical Hacking Tutorial PDF: 204+...
Below is a curated list of Bounty Programs by reputable companies 1) Intel Intel's bounty program...
What is Social Engineering? Social engineering is the art of manipulating users of a computing...
Cybersecurity refers to protecting hardware, software, and data from attackers. It protects...