Ethical Hacking
Learn ARP Poisoning with Examples
In this tutorial we will Learn - What is IP & Mac Address What is Address Resolution Protocol...
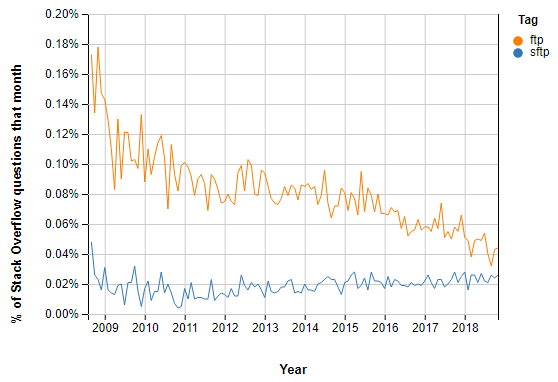
FTP stands for "File Transfer Protocol." It is an internet service which is designed to establish a connection to the specific server or computer. Therefore, users can transfer file (download) or transfer data/files to their computer or the FTP server.
The FTP protocol also includes commands which you can use to execute operations on any remote computer. For example, to change directories, show folder contents, create folders or delete files. It is built on a client-server architecture. FTP allows you to utilize separate control and data connections between the client and server applications. It helps to solve the issue of different end host configurations.
In this tutorial, you will learn
SFTP (full form SSH File Transfer Protocol) is a part of the SSH protocol suite. It provides secure file transfers over SSH to provide access to all the shell accounts on a remote SFTP server.
SSH is a protocol for secure remote access to a machine over untrusted networks. SSH is a replacement for telnet, rsh, rlogin. SFTP verifies the identity of the client and once a secured connection is established information is exchanged.
| Parameter | FTP | SFTP |
|---|---|---|
| Founder | By Abhay Bhushan in 1971 | Tatu Ylönen with assistance from Sami Lehtinen in 1997 |
| Full Form | File Transfer Protocol. | Secure FTP Protocol. |
| Basic | FTP does not offer a secure channel to transfer files between hosts. | SFTP offers a secure channel for transferring the files between the host. |
| Encryption | FTP is accessible anonymously, and in most cases, it is not encrypted. | SFTP encrypts the data before sends it to another host. |
| Architecture used | Client-server | SSH |
| Protocol | FTP is TCP/IP protocol. | SFTP protocol is a part of the SSH protocol which is a remote login application program. |
| Number of channels used | 2 | 1 |
| Commonly used | Yes | NO |
| Transfer method | Direct transfer | Tunneling |
| Inbound Port | Allow inbound connection on port 21 | Allow incoming connections on port 22 |
| Outbound Port | Allows outbound connection to port 21. | Allow outbound connections to port 22. |
In this tutorial we will Learn - What is IP & Mac Address What is Address Resolution Protocol...
$20.20 $9.99 for today 4.5 (112 ratings) Key Highlights of Ethical Hacking Tutorial PDF: 204+...
Mobile Spy Apps or Spyware Apps are smartphone surveillance software. These types of apps help you to...
Ethical Hacking is identifying weaknesses in computer systems/networks and coming with...
What is Digital Forensics? Digital Forensics is defined as the process of preservation,...
Below is a curated list of Bounty Programs by reputable companies 1) Intel Intel's bounty program...