Ethical Hacking
How to Hack WiFi (Wireless) Network
Wireless networks are accessible to anyone within the router’s transmission radius. This makes...
VLAN is a custom network which is created from one or more local area networks. It enables a group of devices available in multiple networks to be combined into one logical network. The result becomes a virtual LAN that is administered like a physical LAN. The full form of VLAN is defined as Virtual Local Area Network.
The below topology depicts a network having all hosts inside the same virtual LAN:
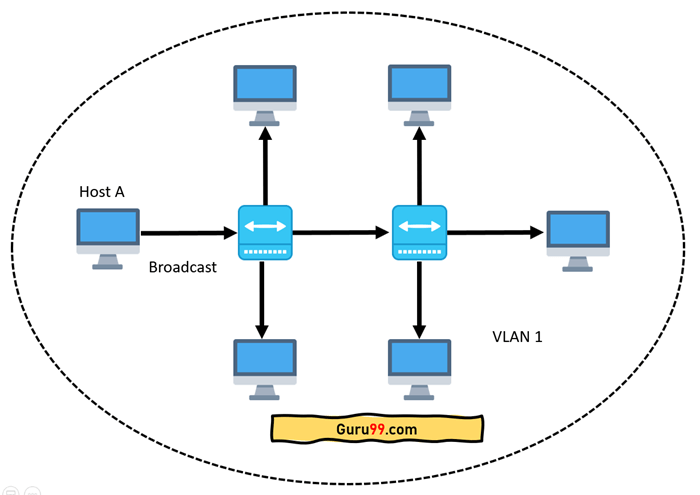
Without VLANs, a broadcast sent from a host can easily reach all network devices. Each and every device will process broadcast received frames. It can increase the CPU overhead on each device and reduce the overall network security.
In case if you place interfaces on both switches into separate VLAN, a broadcast from host A can reach only devices available inside the same VLAN. Hosts of VLANs will not even be aware that the communication took place. This is shown in the below picture:
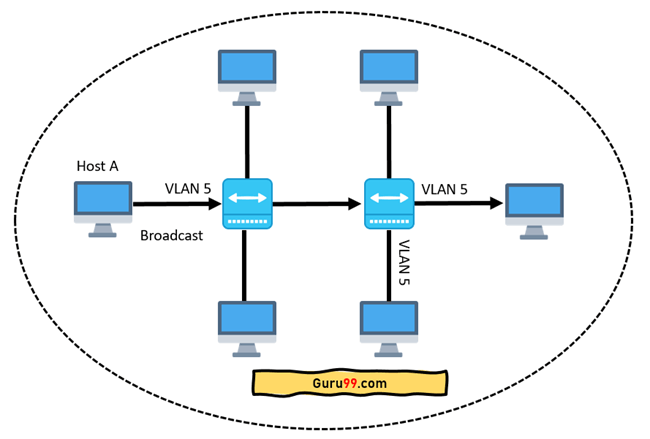
VLAN in networking is a virtual extension of LAN. A LAN is a group of computer and peripheral devices which are connected in a limited area such as school, laboratory, home, and office building. It is a widely useful network for sharing resources like files, printers, games, and other applications.
In this Virtual LAN tutorial, you will learn:
Here is step by step details of how VLAN works:
Here are the important ranges of VLAN:
| Range | Description |
| VLAN 0-4095 | Reserved VLAN, which cannot be seen or used. |
| VLAN 1: | This is a default VLAN of switches. You cannot delete or edit this VLAN, but it can be used. |
| VLAN 2-1001: | It is a normal VLAN range. You can create, edit, and delete it. |
| VLAN 1002-1005: | These ranges are CISCO defaults for token rings and FDDI. You cannot delete this VLAN. |
| VLAN 1006-4094: | It is an extended range of VLANs. |
In the below example, there are 6 hosts on 6 switches having different VLANs. You need 6 ports to connect switches together. It means, if you have 24 various VLANs, you will have only 24 hosts on 45 port switches.

Here are the important characteristics of VLAN:
Here are the important types of VLANs
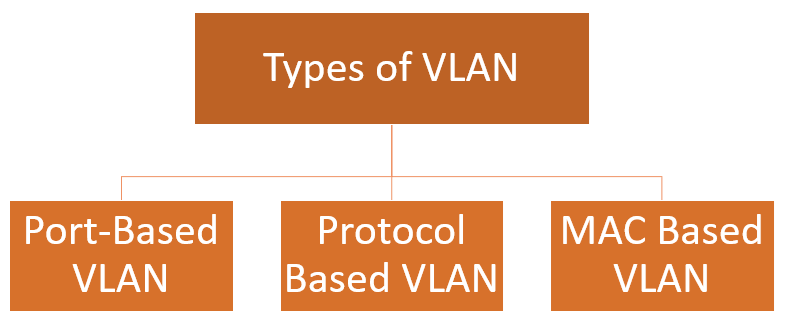
Port-based VLANs groups virtual local area network by port. In this type of virtual LAN, a switch port can be configured manually to a member of VLAN.
Devices that are connected to this port will belong to the same broadcast domain that is because all other ports are configured with a similar VLAN number.
The challenge of this type of network is to know which ports are appropriate to each VLAN. The VLAN membership can't be known just by looking at the physical port of a switch. You can determine it by checking the configuration information.
This type of VLAN processes traffic based on a protocol that can be used to define filtering criteria for tags, which are untagged packets.
In this Virtual Local Area Network, the layer-3 protocol is carried by the frame to determine VLAN membership. It works in multi-protocol environments. This method is not practical in a predominately IP based network.
MAC Based VLAN allows incoming untagged packets to be assigned virtual LAN and, thereby, classify traffic depending on the packet source address. You define a Mac address to VLAN mapping by configuring mapping the entry in MAC to the VLAN table.
This entry is specified using source Mac address proper VLAN ID. The configurations of tables are shared among all device ports.
Here is an important difference between LAN and VLAN:
| LAN | VLAN |
| LAN can be defined as a group of computer and peripheral devices which are connected in a limited area. | A VLAN can be defined as a custom network which is created from one or more local area networks. |
| The full form of LAN is Local Area Network | The full form of VLAN is Virtual Local Area Network. |
| The latency of LAN is high. | The latency of VLAN is less. |
| The cost of LAN is high. | The cost of a VLAN is less. |
| In LAN, the network packet is advertised to each and every device. | In VLAN, the network packet is sent to only a specific broadcast domain. |
| It uses a ring, and FDDI (Fiber Distributed Data Interface) is a protocol. | It uses ISP and VTP as a protocol. |
Here are the important pros/benefits of VLAN:
Here are the important cons/ drawbacks of VLAN:
Here are the important uses of VLAN:
Wireless networks are accessible to anyone within the router’s transmission radius. This makes...
Training Summary An Ethical Hacker exposes vulnerabilities in software to help business owners fix...
IP and Network scanning tools are software that identify various loopholes of network and...
What is CompTIA Certification? CompTIA certifications course are considered one of the most...
Mobile Spy Apps or Spyware Apps are smartphone surveillance software. These types of apps help you to...
Vulnerability scanners are automated tools that constantly evaluate the software system's security risks to...